6 minutes to read
HIPAA compliance testing: strategies to secure healthcare software


Chief Technology Officer
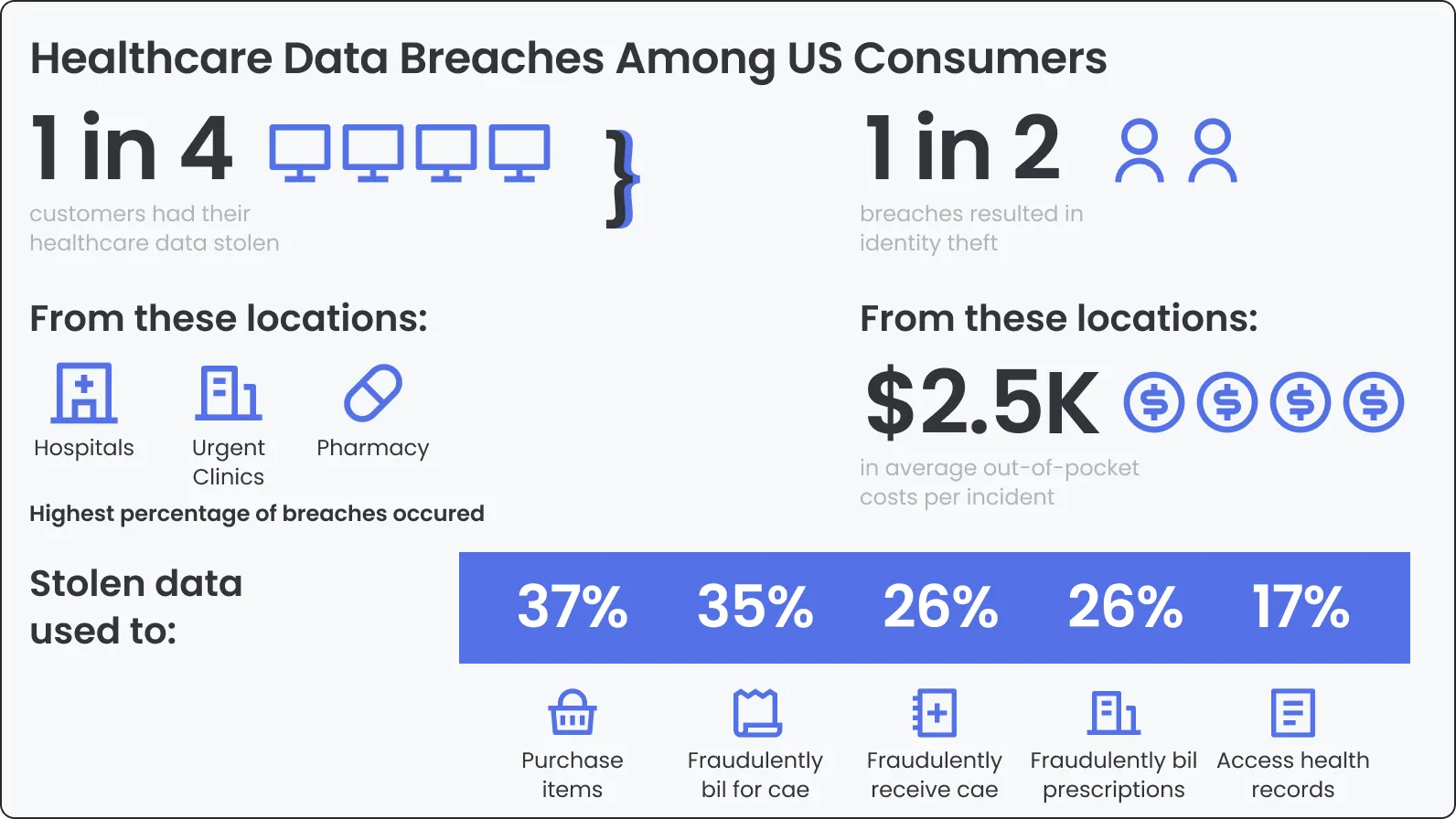
A single data breach in the healthcare industry costs an average of $10.93M. Over 231M Americans have been affected by healthcare data leaks in recent years. With breaches like the 23andMe case, it’s clear that complying with regulations like HIPAA is more important than ever.
If you’re running a healthcare app that handles appointments, prescriptions, or patient data, one security flaw can lead to fines, reputational damage, and lost trust. This is where HIPAA compliance testing services provided by DeviQA comes in. It helps build strong defenses around your product, keeping patient information safe and meeting legal requirements.
What is HIPAA?
Understanding HIPAA is the first step in securing your software. This section explains the legal background and key rules that shape how patient data must be handled.
HIPAA (Health Insurance Portability and Accountability Act) is a U.S. law created in 199 6 to improve healthcare system efficiency and protect patient data. If your software handles electronic protected health information (ePHI), HIPAA applies.
Key areas HIPAA covers:
Together, these rules define how healthcare software must handle patient data.
Navigate all traps and pitfalls of HIPAA compliance with our top-notch testing services
What it means to be HIPAA-compliant
Meeting HIPAA standards goes beyond legal requirements. Here’s what it actually means for your software, team, and organization in day-to-day operations.
Being HIPAA-compliant means meeting strict data privacy and security standards. For software, this includes:
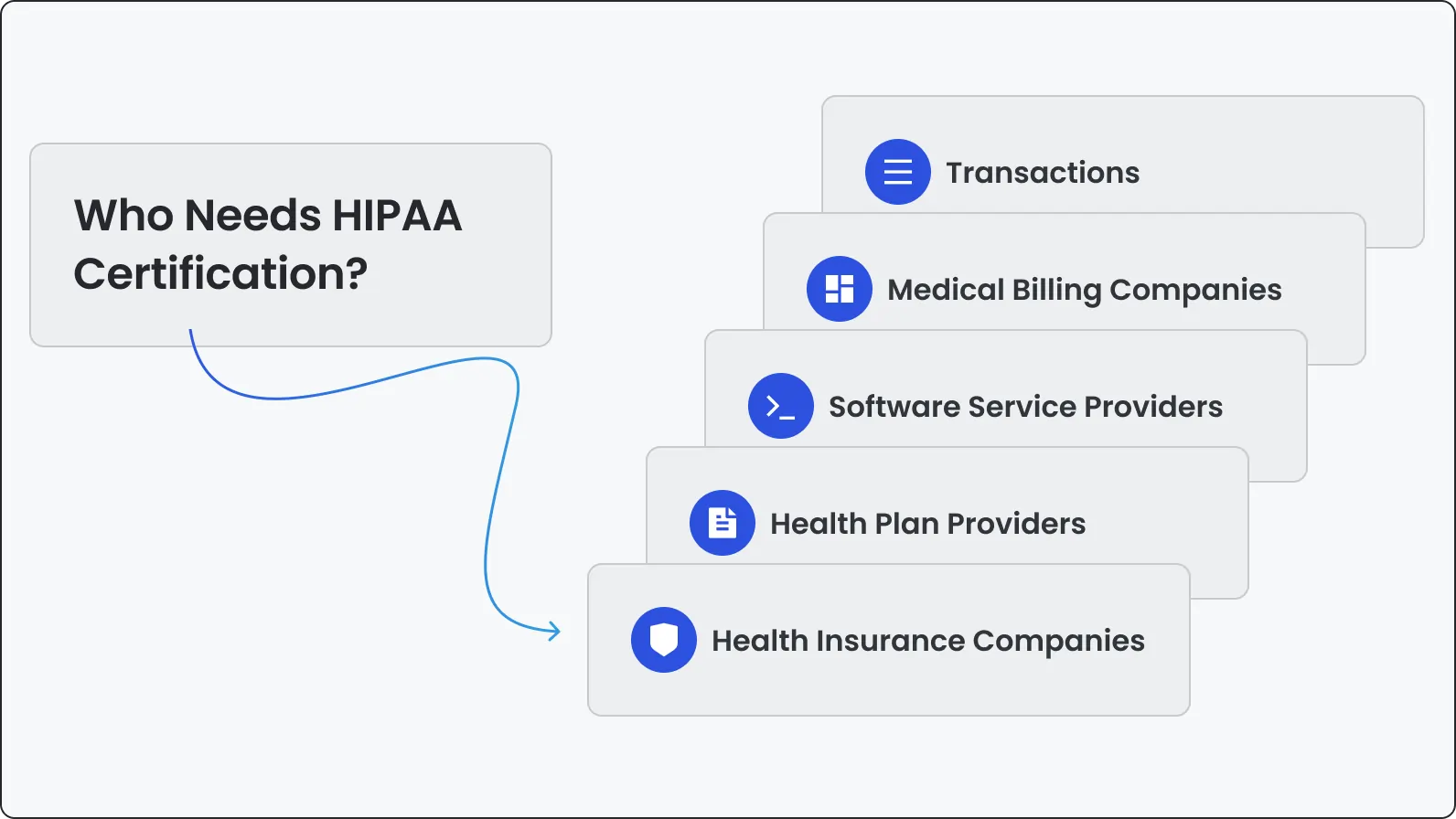
Common HIPAA compliance challenges in software
Building HIPAA-compliant software isn’t simple. Below are common areas where organizations struggle and what makes these areas challenging to manage.
1. Security while scaling
As your app grows, it gets harder to maintain consistent data protection. More users, more data, more risk.
2. Fast-changing software
Agile development means constant updates—each one a potential new vulnerability.
3. Complex data sharing
Healthcare systems often connect across platforms. Data must move securely.
4. User verification
Apps must correctly verify users and control what each can access.
5. Human error
Mistakes still happen—bad permissions, misclicks, overlooked bugs.
6. Changing regulations
HIPAA evolves. Staying compliant requires monitoring regulation updates and adjusting practices.
7. Vendor risk
If your software uses third-party vendors, they must also follow HIPAA rules.
5 HIPAA compliance testing strategies for secure healthcare software
Testing directly influences your ability to meet HIPAA requirements. It validates whether your system enforces the right access controls, protects data, logs activity, and recovers from errors.
1. Security testing
2. Functional testing
Explore DeviQA’s functional testing services
💬 “We often see teams overlook basic workflows under pressure. Functional testing in healthcare must verify every access control, every input field, every log entry.”
— Ievgen Ievdokymov, Senior QA Engineer at DeviQA
3. Third-party vendor testing
4. User acceptance testing
5. Regression testing
Key focus points in a healthcare software testing strategy
These focus areas reflect real-world threats to healthcare data and show how HIPAA requirements shape everything from login flows to infrastructure decisions.
How to be HIPAA compliant with software: Steps to follow
--
💬 “Compliance starts with culture. Processes and checklists matter, but teams that take ownership of data protection go further, faster.”
— Anastasiia Sokolinska, Chief Operating Officer at DeviQA
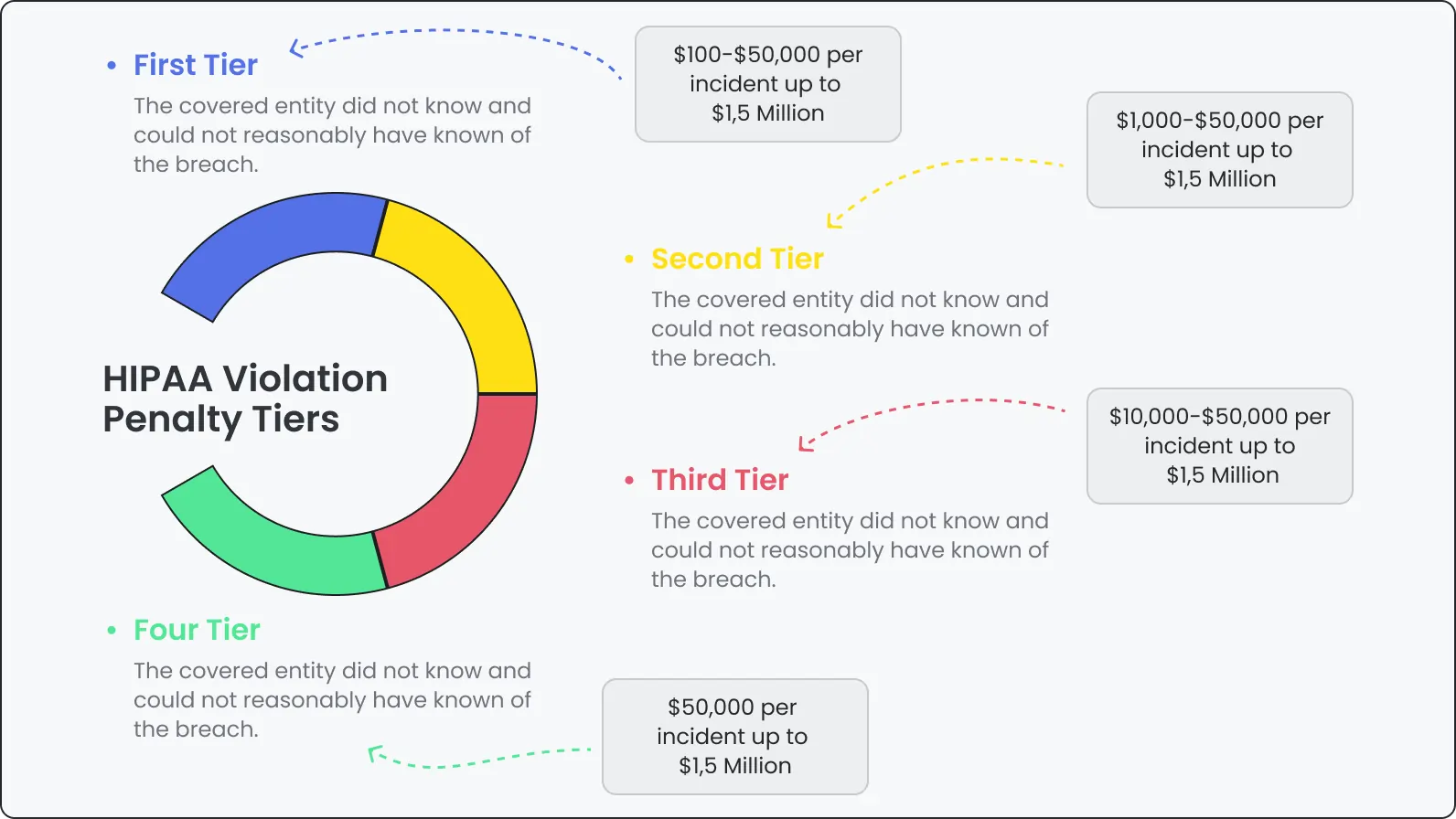
HIPAA compliance testing tools you should consider
Playwright
See Playwright testing services
💬 “Playwright makes a strong case for HIPAA apps with complex UIs. It handles dynamic interfaces better than most frameworks and integrates well into secure pipelines.”
— Dmitry Reznik, Chief Technology Officer at DeviQA
Factors that impact HIPAA compliance testing costs
💬 “Many teams forget that even minor third-party integrations carry big testing overhead. If it touches data, it should be in scope.”
— Mykhailo Ralduhin, Senior QA Engineer at DeviQA
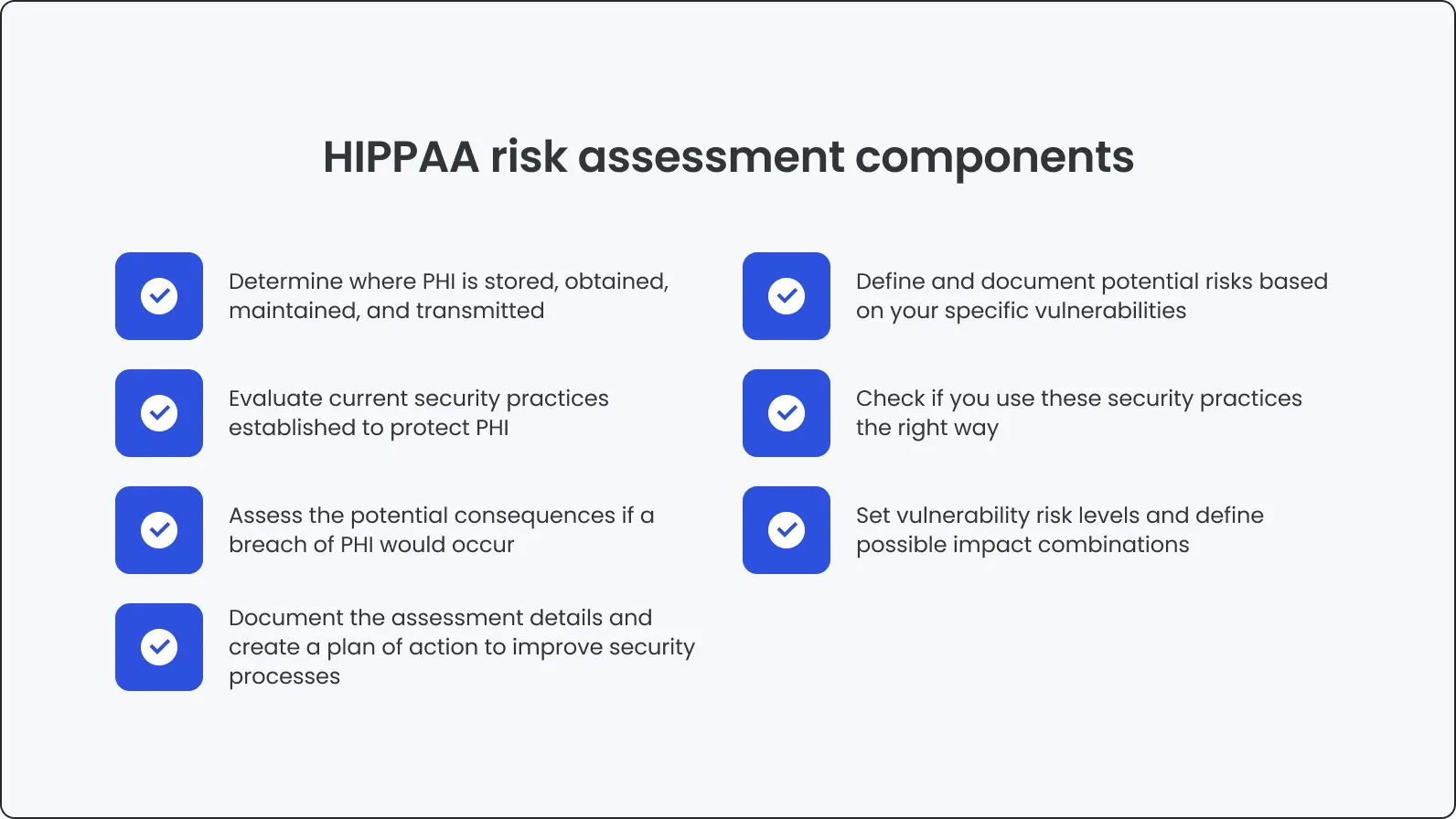
How testing supports long-term HIPAA compliance
As the healthcare industry grows more digital, HIPAA compliance becomes even more critical. These insights should help you plan and prioritize your next steps with clarity.
HIPAA testing is a requirement that directly impacts software quality and trust. It’s part of building software users can trust. Healthcare data is sensitive, and protecting it should be a top priority.
Whether you’re a startup or an enterprise, using the right testing strategies helps reduce risk, improve security, and meet regulatory standards.
Team up with an award-winning software QA and testing company
Trusted by 300+ clients worldwide
