Penetration testing services
Safeguard your infrastructure against cyber threats with our comprehensive penetration testing services.
Minimize the risk of a data breach with DeviQA’s 15 years of penetration testing expertise, providing you with proactive insights into your application’s weak spots.
Trusted by
Our solutions for your penetration testing challenges
At DeviQA, we understand the complexities of maintaining secure protection against modern cybersecurity threats and are committed to helping organizations overcome challenges related to the execution of penetration testing.

Types of penetration testing we perform
Our expert team meticulously examines various security aspects of your systems and applications to identify vulnerabilities before malicious hackers exploit them. Here's a brief overview of the penetration testing types that we perform:
Network penetration testing
Our specialists delve deep into your network infrastructure to uncover weaknesses that could compromise its integrity and confidentiality. We assess routers, switches, firewalls, and other network devices to ensure robust defenses against cyber threats.
Mobile penetration testing
With the proliferation of mobile devices, securing your mobile applications and platforms is crucial. We conduct thorough assessments to identify vulnerabilities in your mobile apps, APIs, and backend systems, protecting your users' data and privacy.
Web application penetration testing
Websites and web applications are prime targets for cybercriminals. Our team conducts detailed assessments to detect all possible vulnerabilities, including SQL injection, cross-site scripting (XSS), and insecure authentication mechanisms. Our goal is to ensure your web assets remain secure.
API penetration testing
APIs (application programming interfaces) are essential for modern software development, although they can also present security risks if not properly secured. We rigorously test your APIs for vulnerabilities, including improper authentication, data exposure, and inadequate access controls, to prevent potential breaches.
Cloud penetration testing
Cloud computing offers numerous benefits, but it also introduces new security challenges. Our experts evaluate your cloud infrastructure, configurations, and permissions to mitigate risks and ensure compliance with the best cloud security practices.
Blockchain penetration testing
Blockchain technology promises enhanced security, but it's not immune to vulnerabilities. We conduct specialized assessments to identify weaknesses in your blockchain implementations, smart contracts, and decentralized applications, safeguarding your digital assets from exploitation.
Social engineering penetration testing
Human error remains one of the most significant security vulnerabilities. Our social engineering tests simulate real-world scenarios to assess your employees' susceptibility to phishing attacks, pretexting, and other social engineering tactics, empowering you to strengthen your organization's security culture.
Elevate your software quality with our cutting-edge QA solutions.
Don’t let software bugs and performance issues jeopardize your reputation. Surpass your competitors with our specialized data-driven QA solutions that ensure detection and rectification of up to 95% of potential issues. Enter your business email below for a free Proof of Concept to start enhancing your software reliability today.


Approaches to the execution of penetration testing

Our security experts can execute penetration testing in three distinct ways to meet the unique needs of your organization:
Black box testing
With black box testing, our expert ethical hackers emulate the actions of cybercriminals, armed with minimal knowledge of your system's inner workings. This approach allows us to simulate real-world cyber threats, identifying vulnerabilities from an outsider's perspective. By mimicking the tactics of potential adversaries, we uncover hidden weaknesses and provide actionable insights to reinforce your defenses.
White box testing
White box testing offers a comprehensive examination of your system's architecture, providing our skilled analysts with full access to internal documentation, source code, and system designs. By leveraging this insider knowledge, we conduct a thorough assessment of your network's strengths and weaknesses to pinpoint vulnerabilities before they can be exploited. With white box testing, you gain unparalleled visibility into your security posture and can make informed decisions on the enhancement of your cyber resilience.
Gray box testing
Gray box testing combines elements of two previously described methodologies, striking a delicate balance between external reconnaissance and internal scrutiny. By simulating the perspective of a partially informed attacker, we emulate the actions of a cybercriminal with limited knowledge of your system's inner workings. This nuanced approach enables us to identify vulnerabilities that may evade traditional testing methods, providing a holistic view of your security landscape.

Choose your cooperation model

We understand that every business has unique needs when it comes to cybersecurity. That's why we offer flexible models of cooperation tailored to suit your requirements. Whether you're a small startup or a large enterprise, we have the perfect solution for you.
Staff augmentation
Whether you need additional manpower for a specific project or want to fill skill gaps within your team, we can provide the right talent to complement your in-house capabilities.
Best option for: businesses with fluctuating penetration testing needs or those seeking to augment their existing teams with specialized skills for short-term projects.
Easily adjust your team to evolving project demands without hiring full-time employees.
Avoid the recruitment and training costs associated with hiring new employees.
Quickly onboard experienced testers, reducing the time needed to kick-start or complete your projects.
Dedicated team
A dedicated team becomes an extension of your in-house team and strictly adheres to your workflows and corporate policies.
Best option for: large enterprises or organizations with ongoing or complex penetration testing needs requiring dedicated resources and close collaboration.
Assemble a dedicated team with the specialized skills needed for your specific project.
Directly oversee and manage your dedicated team, ensuring alignment with your objectives and timelines.
Enjoy seamless integration, close collaboration, and high efficiency.
Outsourcing
Our team handles everything from test planning and execution to reporting, providing you with comprehensive cybersecurity solutions without the need for in-house resources.
Best option for: small to medium-sized businesses looking for cost-effective testing services and convenience without compromising on quality.
Let us handle your cybersecurity needs and free up your internal resources to focus on core business activities.
Avoid the costs associated with maintaining an in-house QA team.
Tap into the expertise of our seasoned professionals, who stay updated with the latest industry trends and best security practices.
DeviQA’s AI advantage
At DeviQA, we use AI to make testing smarter and simpler. Our ecosystem is built to deliver faster, smarter, and more cost-efficient results — so your team can do more in less time.
DeviQA AI ecosystem

AI-powered IDE assistant
Reduces test script writing time

QA companion
Provides suggestions for test optimization and addresses gaps

Automated code review
Flags unused variables, improper loops, and other common errors

AI for API testing in Postman
Streamlines API test case creation and response validation
Features
Test case creation
Code review
Exploratory planning
Log analysis
Testing time spent
without AI
6 hrs
3 hrs
2 hrs
2 hrs
Testing time spent
with DeviQA AI
4 hrs (30% saved)
2 hrs (40% saved)
45 min (60% saved)
1 hr (50% saved)
Our approach to penetration testing

Thorough assessment
We begin by thoroughly assessing your organization's infrastructure, applications, and network architecture. This helps us identify potential vulnerabilities and weak points that could be exploited by malicious hackers.
Methodical testing
Our team of highly skilled ethical hackers employs industry-leading methodologies and cutting-edge tools to simulate real-world cyberattacks. We leave no stone unturned in our pursuit to uncover any vulnerabilities that could compromise your systems.
Customized solutions
We recognize that every organization has its own challenges and requirements when it comes to cybersecurity. That's why we tailor our approach to penetration testing to align with your specific goals, industry regulations, and risk tolerance level.
Comprehensive reporting
On the completion of our penetration testing activities, we will provide you with detailed reports that outline our findings, along with actionable recommendations for remediation. Our reports are clear, concise, and designed to empower you with the insights needed to strengthen your cybersecurity posture.
Ongoing support
Cyber threats are constantly evolving, which is why we offer ongoing support to help you stay one step ahead of potential attacks. Whether it's implementing security patches, conducting regular retests, or providing training for your staff, we're here to support you every step of the way.
Commitment to excellence
At DeviQA, we're committed to excellence in everything we do. We deliver penetration testing services with the utmost professionalism, integrity, and dedication to ensure the security and resilience of your digital assets.
What you get
Feel the improvement in
3 days
Reduction in your costs
60%
Accelerate development by
30%
Automation faster in parallel by
56x
Increase test coverage to
95%

We serve

Our expertise and resources allow us to cover the unique needs of each project, ensuring the delivery of high-quality software that meets users’ requirements and business goals.
Book a call to meet industry compliance requirements and demonstrate robust security measures to stakeholders
Here’s what people are saying
about DeviQA
QA tools & platforms we hold expertise in
Playwright
Cypress
Cucumber
Selenium
Appium
Mocha
Robot Framework
SpecFlow
TestNG
WebdriverIO

Selenide
Calabash

Watir
Codeception

HCL AppScan
Nessus

NMAP
BurpSuite

Acunetix

OWASP ZAP

Metasploit
Wireshark

DBeaver
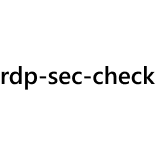
Rdp-Sec-Check

SNMPCHECK

AiR

SSLSCAN
k6

JMeter

Load Runner

Visual Studio

Rest API

GraphQL

Apiary

Bluetooth Low Energy API

Apple Pay

Google Pay
Apple Maps
Fingerprint API

Postman
Swagger

Charles Proxy

Ready API

ACCELQ

Katalon Platform

REST-Assured

SQL Server

MySQL

Oracle

PostgreSQL

Cassandra

MongoDB

RethinkDB

Amazon S3

Redshift

DynamoDB

Amazon RDS

DocumentDB

Amplify

Lambda
Amazon EC2

Elasticache

Azure Datalake

Blob Storage

CosmosDB

SQL Database

Synapse Analytics
Google Cloud SQL

Google Cloud Datastore

Awards and recognitions

Collaboration process overview
Initial contact
During our initial call, we aim to understand your testing requirements and goals
Assessment
We evaluate your current testing process and create a tailored plan to enhance it
Proof of concept
We offer a complimentary proof of concept, allowing you to experience our proficiency and expertise
Trial and evaluation of performance
We start a trial period with you, and once complete, we review the results together and discuss options
Contract signing and full-scale QA implementation
Upon mutual agreement, we move forward with the QA process by signing a contract and beginning work
Partnership with flexibility
Our engagement options give you commercial flexibility to dial up and dial down resources depending on your own needs
Let’s schedule a call
Flexible collaboration options allow you to choose the level of support that best meets your needs
Questions & answers

What types of penetration tests do you offer?
We offer web application testing, API security testing, internal/external network penetration testing, cloud pentesting, and social engineering simulations.
How is penetration testing different from vulnerability scanning?
Vulnerability scanning is automated and identifies known issues. Penetration testing is manual, simulating real attacker behavior to uncover hidden risks.
Do you follow any pentesting standards?
Yes. We follow OWASP Top 10, PTES, NIST, and OSSTMM frameworks to ensure thorough and compliant penetration testing procedures.
Can you help with compliance requirements?
Absolutely. Our pentesting supports compliance with GDPR, HIPAA, PCI DSS, ISO 27001, and SOC 2 by providing detailed reports and risk remediation plans.
How often should penetration testing be performed?
We recommend at least once a year or after any major code updates, infrastructure changes, or deployments of new features.
Why choose DeviQA for penetration testing?
DeviQA’s cybersecurity team combines deep testing expertise, real-world attack simulations, and actionable reporting to strengthen your defenses.




























